Protecting Applications from the Inside
Virsec delivers a radically new approach to security, protecting enterprise applications from the inside against today’s most dangerous cyber threats. The Virsec Security Platform (VSP) definitively stops fileless and in-memory exploits that bypass conventional security, delivering unprecedented speed and accuracy, while eliminating false positives.
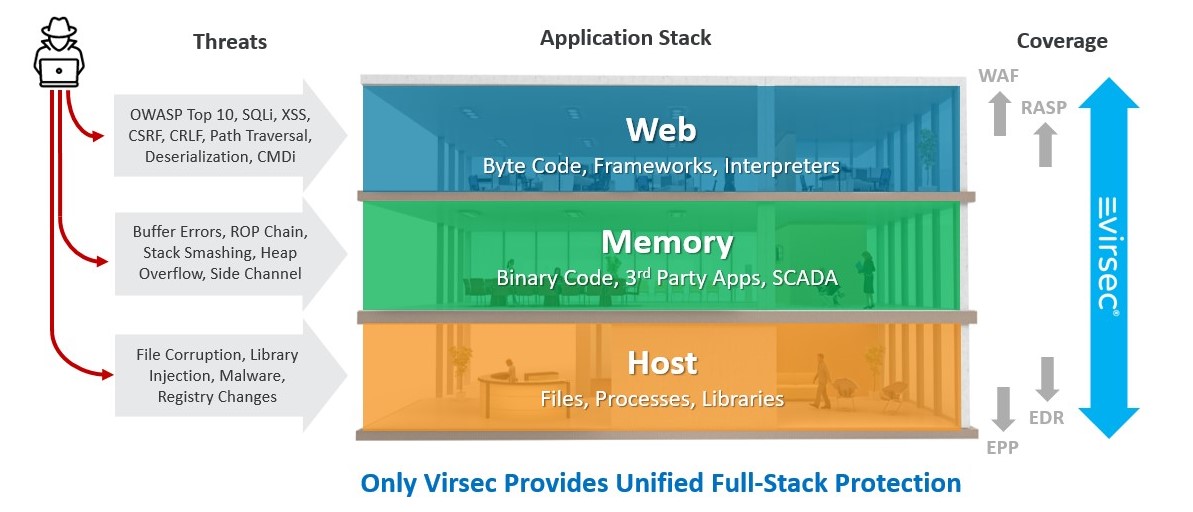
Complete App-Stack Protection
Attackers are adept at finding vulnerabilities and they can easily bypass point solutions such as WAF, EPP and EDR that don’t see the bigger picture. We are here to protect the entire attackable surface of the application including Web, Memory, and Host. VSP detects and stops the widest spectrum of attacks including OWASP Top 10, memory errors, library injections, process corruption, malware and much more.
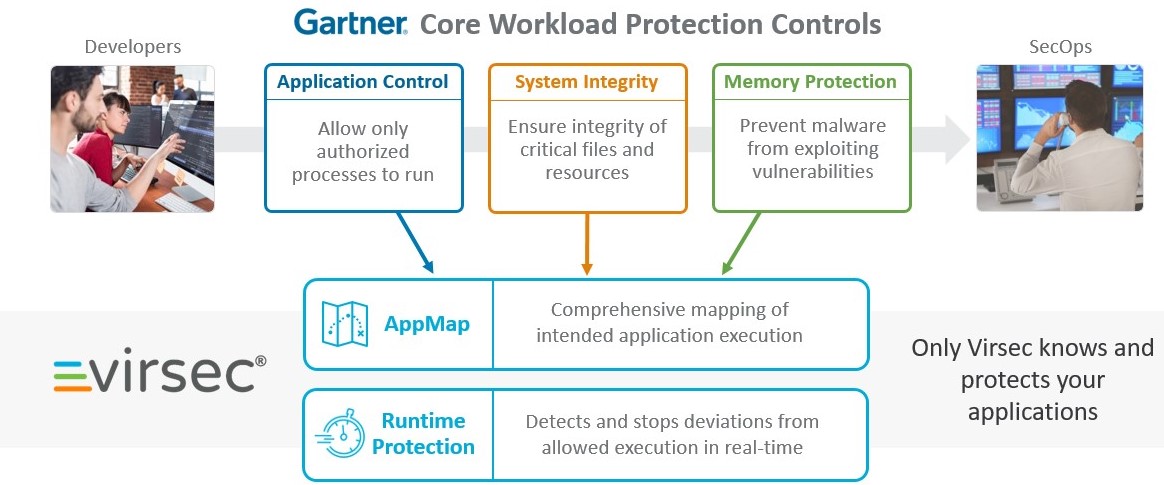
Memory Protection is “Mandatory”
Analyst firm Gartner states that memory protection is “mandatory” for workloads and recognized Virsec Security Platform for providing advance capabilities to intergrate three core areas recommended by Gartner: